In this blog we are going to see about ethical hacking tools that are usefull in performing pentesting of wireless interfaces, websites, apps and etc. First we are going to see tools related to Wireless hacking, exploitation, information gathering, social engineering, Password Cracking, Forensics and Vulnerabilty Scanning.
1. Wireless Hacking
a. Aircrack-NG
It is a complete collection of tools designed to assess Wi-Fi network security. It focuses on different areas of Wi-Fi security such as monitoring, attacking, testing, and cracking. It supports WPA/WPA2-PSK key cracking via dictionary attacks.
b. Wifite
Wifite is an automated wireless attack tool. It simplifies the process of launching attacks on WEP, WPA, and WPS encrypted networks using tools like Aircrack-NG, Reaver, and others.
c. Kismet
Kismet is a wireless network detector, packet sniffer, and intrusion detection system. It works with Wi-Fi (802.11), Bluetooth, and other radio protocols, making it invaluable for wireless network auditing.
d. TCPDump
TCPDump is a powerful command-line packet analyzer. It allows users to capture and analyze network traffic in real-time, making it essential for diagnosing network issues and security testing. It is already installed in kali linux.
e. Reaver
Reaver is a tool designed to exploit the WPS vulnerability in wireless routers. It performs brute-force attacks to recover WPA/WPA2 passphrases, targeting poorly configured networks.
2. Exploitation
a. Burp Suite
Burp Suite is a toolkit for web application security testing. It allows penetration testers to identify vulnerabilities like SQL injection,CSRF, Command injection, XSS, and more through an proxy and various automated tools. This contains many tools inside it like intruder, proxy, repeter and etc.
b. Metasploit Framework
Metasploit is a popular framework for developing, testing, and executing exploit code. It is widely used for penetration testing, enabling security researchers to identify and exploit vulnerabilities in systems.
c. SQL Map

SQLMap is an penetration testing tool that automates the detection and exploitation of SQL injection vulnerabilities. It also helps in database fingerprinting, data fetching, and accessing the file system.
d. ZAP

ZAP is an open-source web application security scanner. It helps find security vulnerabilities in web apps during development and testing phases, offering automated and manual testing features.
e. ExploitDB
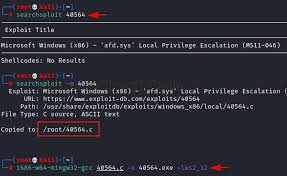
ExploitDB is a archive of exploits and proof-of-concept code for known vulnerabilities. It is a valuable resource for security researchers and penetration testers to stay updated on new threats.
3. Information Gathering
a. Nmap

Nmap (Network Mapper) is a network scanning tool used for network discovery tool. It can detect live hosts, open ports, running services, and operating systems.
b. Shodan
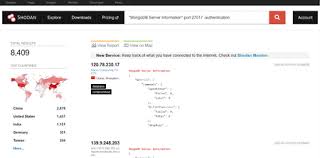
Shodan is a search engine for Internet-connected devices. It helps security professionals discover exposed systems, IoT devices, and potential vulnerabilities across the internet. It can find anything which is connected with internet from mobile phones to microwaves.
c. Maltego
Maltego is a infomation gathering and visualizing information about people, companies, domains, and more. It is widely used in OSINT investigations.
d. Recon-ng
Recon-ng is a web reconnaissance framework written in Python. It provides a powerful environment to conduct open-source web-based reconnaissance quickly and efficiently.
e. Amass
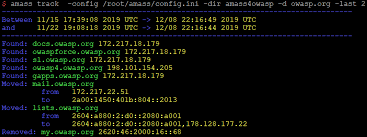
Amass is a powerful tool for network mapping and external asset discovery. It aids in DNS enumeration, subdomain discovery, and mapping attack surfaces.
4. Software Engineering
a. GoPhish
GoPhish is an open-source phishing framework designed for security awareness training. It helps organizations simulate phishing attacks to assess employee susceptibility to social engineering.
b. Hidden Eye
Hidden Eye is a modern phishing tool with advanced features for creating realistic phishing pages targeting various platforms.
c. Social Fish
SocialFish is an advanced phishing tool designed for social engineering attacks. It allows the creation of fake login pages to capture credentials for educational purposes
d. EvilURL
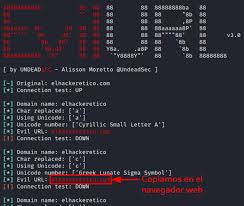
EvilURL is a tool to generate and detect look-alike domains for phishing campaigns, helping identify homograph attacks.
e. Evilgnix
Evilginx is a man-in-the-middle attack framework used for advanced phishing attacks. It captures credentials and session cookies, bypassing 2FA protections.
5. Password Cracking
a. John The Ripper

John the Ripper is a fast password cracker used for recovering weak passwords from hashes. It supports various encryption algorithms and is highly customizable for password cracking.
b. Hydra

Hydra is a powerful network login cracker supporting numerous protocols. It performs brute-force attacks to identify weak credentials on services like FTP, SSH, HTTP, and more.
c. Hashcat

Hashcat is an advanced password recovery tool known for its speed and efficiency. It supports brute-force, dictionary, and hybrid attacks on hashed passwords using CPU or GPU.
d. OPHCrack
OphCrack is a Windows password cracker based on rainbow tables. It can recover passwords quickly without needing brute-force methods.
e. Medusa
Medusa is a speedy, parallel, and modular login brute-forcer supporting various protocols. It is designed for large-scale brute-force attacks.
6. Forensics
a. Autospy

Autopsy is a digital forensics platform for analyzing hard drives and smartphones. It helps recover deleted files, analyze emails, extract web artifacts, and more.
b. GuyMager
GuyMager is a forensic imager for acquiring and verifying disk images, widely used in digital forensic investigations.
c. Foremost
Foremost is a console program for recovering files based on their headers, footers, and internal data structures. It is used in data recovery and forensic analysis.
d. Binwalk
Binwalk is a tool for analyzing binary files to extract embedded data and reverse-engineer firmware images.
e. Wireshark
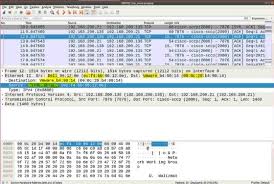
Wireshark is a network protocol analyzer that captures and displays packet data in real-time. It is widely used for network troubleshooting and forensic investigations.
7. Vulnerabilty Scanning
a. OpenVAS
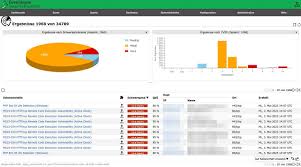
OpenVAS is an open-source vulnerability scanner that detects security issues in systems and applications. It provides detailed vulnerability assessment reports.
b. Nessus

Nessus is a popular vulnerability assessment tool that helps identify vulnerabilities, misconfigurations, and compliance issues across IT environments.
c. AppScan

IBM AppScan is a commercial security testing tool for web applications. It identifies vulnerabilities related to security standards like OWASP Top 10.
d. Retina
Retina is an enterprise vulnerability management solution designed for vulnerability assessment, patch management, and compliance reporting.
e. Nexpose
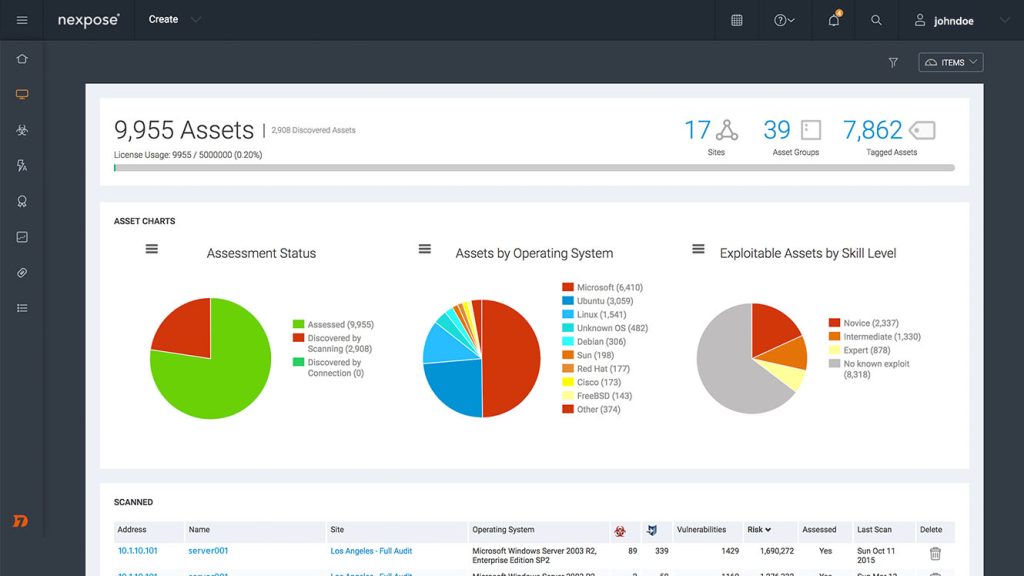
Nexpose by Rapid7 is a vulnerability scanner that helps security teams identify, assess, and remediate vulnerabilities in real-time.